Introduction
In the world of automation, Programmable Logic Controllers (PLCs) are ruggedized industrial computers that have been at the forefront of manufacturing processes since the late 60’s. Due to their ability to run mission-critical applications for years and even decades, PLCs are often seen as trusted computers within manufacturing plants. With the rollout of the internet in the 90’s, PLCs were introduced to a mirage of cybersecurity vulnerabilities due to the extremely low security of the Modbus TCP/IP protocol, the de facto protocol that PLCs use to communicate

The purpose of this project is to demonstrate just how vulnerable these mission-critical computers are by implementing a plant irrigation system using PLC software within a network. A command injection attack will be executed against our PLC network to exploit the vulnerabilities of the Modbus protocol.
Methodology
OpenPLC, and open-source PLC software that can be used with microcontrollers and Raspberry Pi’s, will be our main platform to emulate a PLC with our Raspberry Pi. This platform will turn our Pi into a fully-fledged PLC that can run Ladder Diagrams / Structured Text programs and communicate using the Modbus TCP/IP protocol.
The goal of the irrigation system is simple: Water the plants to keep them alive. If the moisture sensor detects the plants are dry, turn on the pump to water the plants. If the program detects the tank is empty, the inlet valve will turn on and rush water into the tank from a water source.
Our project will have two methodologies:
- Software Simulation – The irrigation system will be simulated using SCADABr, an open-source SCADA (supervisory control and data acquisition) webapp. SCADA is a protocol used by industrial control systems engineers to monitor and control industrial processes in real time, usually from remote locations.
- Hardware Simulation – The irrigation system will be simulated using real hardware. The hardware simulation will be slightly different compared to the software simulation, but with the same purpose.
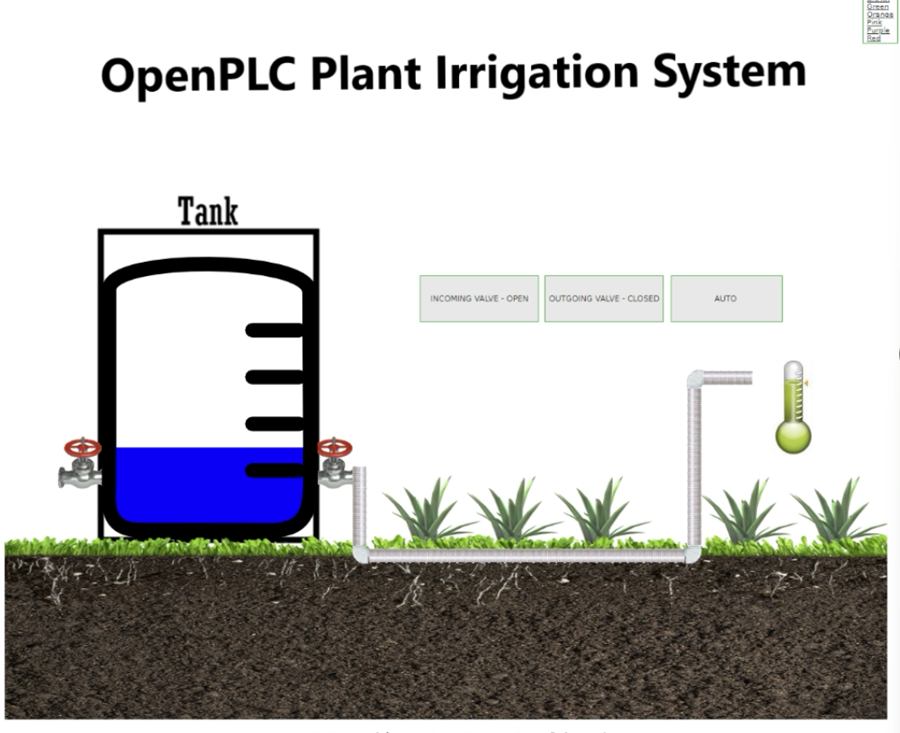

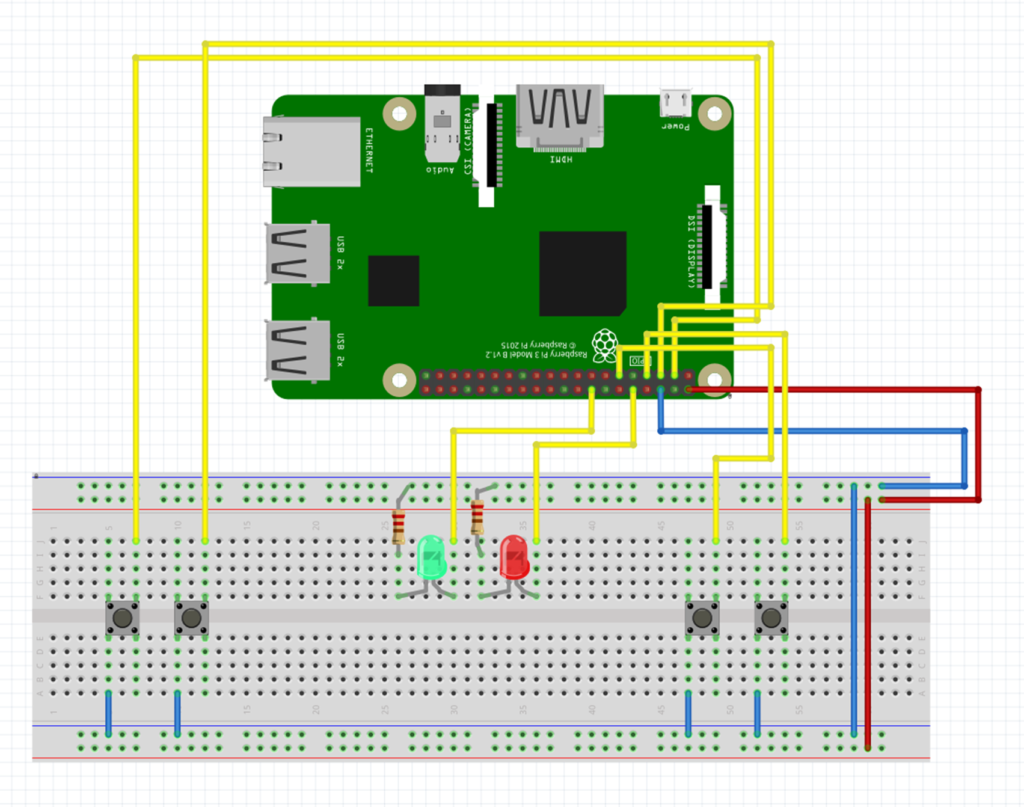
Equipment Used
- Raspberry Pi
- Push Buttons (4)
- LEDs (2)
- 4-Relay Board
- Water Float Sensors (2)
- Water Container (2)
- 3D Printed Farm
- 12v Adapter (2)
- Solenoid Water Vaules (2)


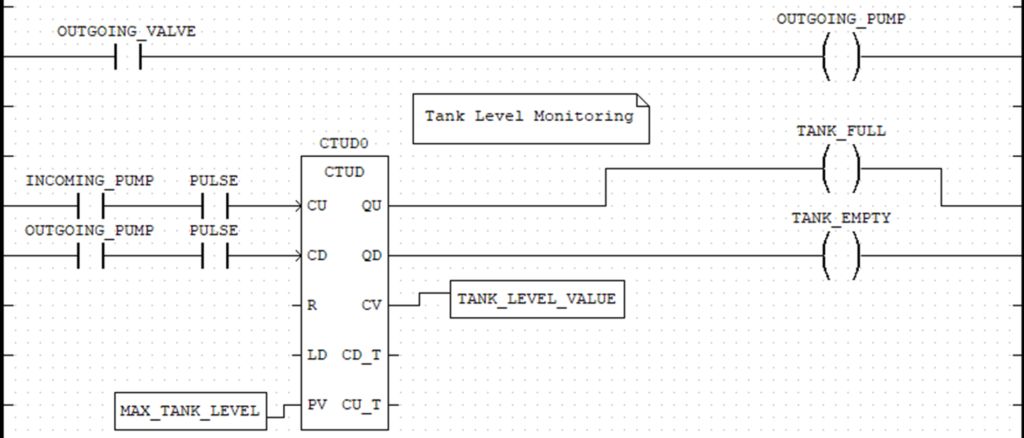
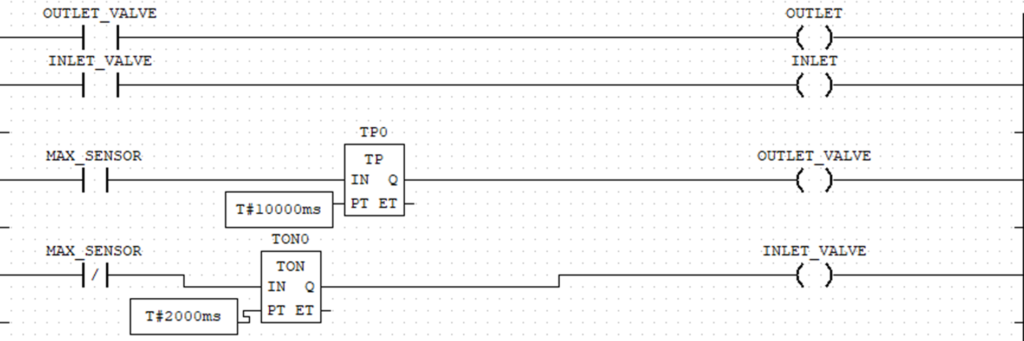
Ladder Diagrams
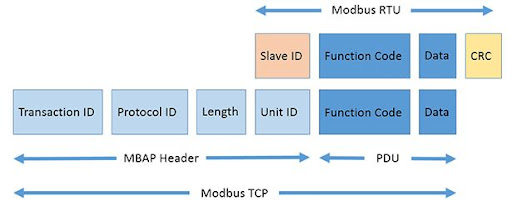
Modbus TCP/IP Protocol
Why Modbus is vulnerable:
- Lack of Confidentiality: All Modbus messages are transmitted in clear text across the transmission media.
- Lack of Integrity: There is no integrity check built into modbus application protocol. Depends on lower layer protocols to preserve integrity.
- Lack of Authentication: There is no authentication at any level of the modbus protocol
Because of these vulnerabilities, we crafted a malicious Modbus packet to be sent hundreds of times per second to flood the PLC with commands, hence the name Command Injection Attack. Our attack will focus on turning on the outlet valve indefinitely, causing the plants to be inundated if it were to happen in real life
Conclusions
In conclusion, we exploited Modbus’s vulnerabilities and overloaded the PLC (Raspberry Pi) with malicious commands. While other protocols such as HTTP/1.1 have evolved over time to their newer, more secure iterations (HTTP/3), Modbus has remained stagnant. As a result, industrial control systems, such as Programmable Logic Controllers (PLCs), remain persistent targets for potential attackers to exploit, particularly due to their operation of critical applications capable of causing widespread damage, such as the disruption of entire cities.
Citations
Openplc Overview. Página Inicial, https://openplcproject.com/docs/openplc-overview/.
“OpenPLC.” YouTube, YouTube, https://www.youtube.com/@openplc.
Raspberry Pi Plant Watering (& Time Lapse).” YouTube, YouTube, 18 July 2021, https://www.youtube.com/watch?v=_NTW0npN4N0&ab_channel=ExplainingComputers.
Leave a Reply